Video surveillance for virtual machines and Docker containers

Presently, virtual machines are massively used by individuals and businesses around the globe, for various reasons and in various scenarios including but not limited to video surveillance installations. If you haven’t heard of virtual machines, the next chapter will help you get the insight into what is a virtual machine, and why millions of users and companies are already taking advantage of the technology benefits.
Virtual machines explained in simple words
A virtual machine (also called a VM for short) is the emulation (or virtualization) of a computer system that exists on a physical machine, uses its resources and hardware, and provides functionality of a real computer. There might be multiple such ‘duplicates’ powered by one or several hypervisor software on a single physical machine, isolated and working independently from one another. Ever rented a Cloud server? This is most probably a virtual machine inside a physical machine sitting in a data center somewhere.
The technology originated from the time-sharing principle introduces in 1960s that used to allowed multiple users to use a computer at the same time, which explains one of the purpose of using a virtual machine – sharing of resources for various tasks inside one machine. That purpose is usually the primary for when a VM is used in corporate systems.
Private individuals tend to use VMs primarily for security reasons facilitated by virtual machines isolated work.
There is a third reason for using virtual machines that can be of great current interest to both private and business sector – VMs allows to emulate alien operating systems inside another. For example, when some essential industry-specific computer programs only run in Windows OS while the work machines are all Macs.
Docker is a type of virtual machine implementation on the level of operating system enabling multiple isolated and secure virtualized servers to run on a single physical server. A Docker uses software delivered in containers – isolated bundles of software, configuration files, and required libraries – that communicate with each other through specific defined channels. Usually Dockers use less system resources than regular virtual machines.
What is the problem with virtual machines

If virtual machines are such an effective, isolated and secure thing, then why doesn’t everyone use it?
As we have established above, virtual machines and Dockers are not real machines, they are emulation of one, an environment. Which confuses many programs that need to get information about the machine they are working on, or to utilize systems resources they do not have access to. For example, if a program is designed to work with web camera images, it might not do what it is supposed to do in a virtual machine that doesn’t have the rights to access USB devices.
Besides, running virtual machines can be CPU-intensive on some weaker computers, so it probably won’t be a great idea to create a virtual machine to run top video editors notorious for their hungry requirements.
As for Dockers, not each program supports work in one as it might structurally need to access resources, libraries, files that are not included into their own container. In such a case it might work perfectly well in a real computer and fail to work properly in a container – and not every manufacturer dedicated to spend precious resources and time on developing a workaround for Dockers, if that is not what forms a substantive share of their market.
Video surveillance in virtual machines
Luckily, there are video surveillance solutions in the market that can work in a virtual environment as well as on physical machines. Xeoma is one of such software that helps have a video surveillance system running in a virtual machine or Docker. If you haven’t yet heard about it, here is an extensive presentation of Xeoma.
Xeoma has a Trial version with almost all features that doesn’t require licensing so it might work in either physical or virtual machines without any difference. If a Trial edition of Xeoma is used, the only VM-connected concern might be accessing USB cameras (web cameras). If you are going to use Xeoma with USB cameras in your virtual machine, simply make sure that the VM has access to USB devices.
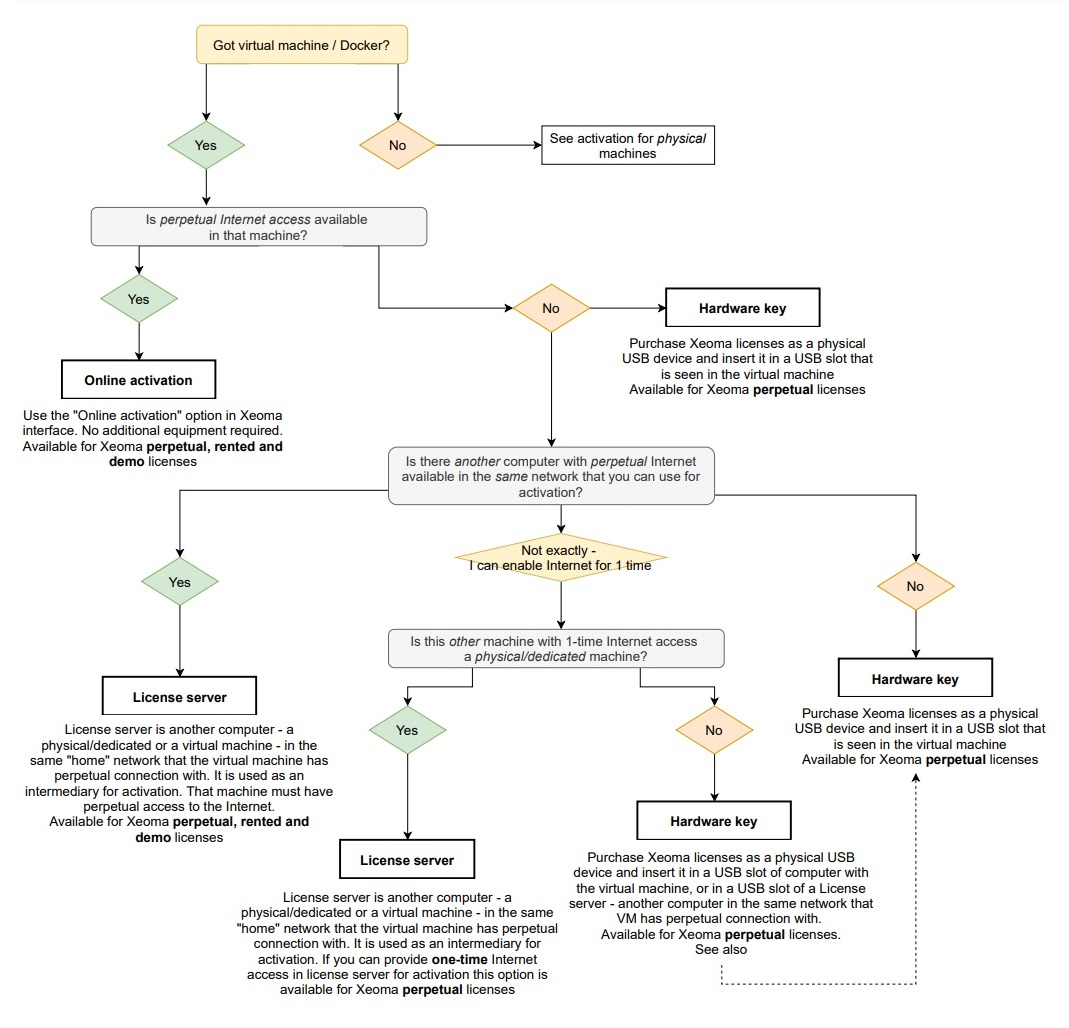
Xeoma also has 4 commercial editions (Xeoma Pro, Xeoma Standard, Xeoma Lite, Xeoma Starter*) that require activation – and they too work in virtual machines. Xeoma has several types of licenses (perpetual, rented or demo licenses) and there are several options for activation of each of them. In most cases the easiest way to activate Xeoma licenses is to have permanent Internet access enabled in the VM or Docker system. Sometimes – especially in banks, governmental or military organizations – Internet access is restricted but Xeoma has such cases covered too! With hardware keys and/or license server options video surveillance systems can work in virtual machines even in such isolated distributed systems.

|
Xeoma free rebranding tool also works on virtual machines! Learn more here |
Online activation:
After you obtain a Xeoma license, you will get an alphanumeric license key that should be entered in Xeoma’s “Activate” tab or through a console command. This method works for virtual machines too if they have permanent Internet access. This method works for perpetual, rented and demo licenses (including Renewals, and Upgrade from Standard to Pro).
License server:
Using another machine – virtual or physical – in the same home network with the VM you need the licensed Xeoma on to send activation requests through and pass the responses to VM. That other machine should have Internet access and constant network connection to the VM with Xeoma. In simple words, the principle is to delegate the activation to another machine (even as small as a single-board micro computer or even a smartphone) that can seed the activated license to a virtual machine with video surveillance. Available for perpetual licenses (one-time Internet connection required) and rented or demo licenses (perpetual Internet connection required).
Read more about network activation with a license server
Hardware key:
When the virtual machine or Docker with Xeoma video surveillance has no Internet connection, and there is no computer in the same network with constant connection to that VM that could be an intermediary for activation, you can use a hardware key license instead of a regular ‘software’ form of license Xeoma is supplied in. A hardware key is a USB device that should be inserted into a USB slot of the computer with Xeoma and VM. Disadvantage: extra fee for the device and shipping, in addition to the cost of the actual Xeoma license or licenses. See prices here
Here is a diagram that will help you get the right activation option for your environment:

|
Read also: feedback from Xeoma user- ‘Xeoma Video Surveillance Docker Container.’ |
Unique video surveillance software that works in virtual machines
Xeoma is the modern-day video surveillance solution that aligns with all contemporary video security and business tasks. The type of machine doesn’t affect performance of Xeoma.
Xeoma video surveillance software has over 100 features, including several dozens of smart video analytics that are also eligible in virtual machine environment.

Face Recognition: basic and AI option

Face Recognition: unique visitors counter

Emotion recognition

FaceID

Object recognition

Smart-card reader

QR Code recognition

SmartHome RIF+

Color recognition

License plate recognition

Crowd detector

Sports ball tracking

Gender recognizer

Age recognizer

Object Recognition: Seabird option

Object Recognition: Drone and Airplane option

Vehicle speed detector

Sound events detector

Face recognition: Mask Detector option

Construction site safety

Modbus controllers

Text Recognition

Slip and fall detector

Eye tracking

Parking spots

360° surround view

Vehicle Speed Detector

Sending ANPR results through FTP

Loitering Detector

Smoke and Fire Detector

Detector of Abandoned Objects

Cross-Line Detector

Privacy masking

RTSP Broadcasting

Button Switcher
Move to PTZ preset
• PTZ presets and tours
• PTZ control in browser
• Choice of users for the PopUp Window
• Clients update automatically
• Sound alarm on clients
• Making intervals of archive undeletable
• Simultaneous view of several archives
• Synchronized export of several archives
• Heatmap
• Multilayered e-Map
• Support for LDAP
• Support for IP microphones
• Support for webRTC
• Support for USB joysticks
Most features are available for Windows and Linux families so a virtual machine can be used to enable them, for example, on a Mac.

|
Xeoma has support for P2P technology of some P2P cameras – but only under Windows 32-bit. If you don’t have such an OS you could create a VM with one, and try the feature. |
- Banks, pawn shops and financial organizations
- Airports, railway or underground stations, and similar places of public gatherings
- Shops, malls, retail and wholesale stores
- Advertisement and promo stands, billboards, banners
- Beauty parlors, hairdresser shops, nail bars and similar services
- Restaurants, café, and similar HoReCa establishments
- Yoga and spa centers
- Hotels, hostels, motels, etc.
- Offices, call centers, etc.
- Open air public events (meeting, concert)
- Safe city programs (detection of gunshots, screams, aggressive behavior, people falling down, etc.)
- Police, road safety (search for missing vehicles or people, fine-imposing system for traffic violations)
- Education: schools, universities and campuses, kindergartens, art and dances courses
- Medical organizations (hospitals, walk-in medical offices, ambulance vehicles)
- Public and cargo transportation
- Construction businesses
- Production, mining, drilling (automation and optimization)
- Farming (crops, fish, cattle, etc.)
- Seafaring, cruise ships, ports
- Military and army
- Entertainment (zoo, bowling, stadiums)
- Smart home systems
- Control of access to private, commercial or governmental territories
- Private uses (surveillance over nanny, elderly, children, workers, etc.)
- and many more!
Creating a virtual machine for video surveillance might prove to be an effective modernization and integration policy in both private and business systems. In many top-security businesses, virtual machines can be an integral part of larger security and overall business frameworks where duties of video surveillance extend across processing vast amounts of video data from high-definition cameras, creating safer spaces, detecting events and sending out immediate alerts, to analyzing customers’ flows and preferences, generating data for better-performing campaigns, and providing real-time insight about performance of a business.
As Xeoma video surveillance software that supports 99% of cameras in the market and all major operating systems (including on ARM-based architecture) does support work with virtual machines and offers multiple solutions to activation challenges, both individuals striving for cyber security and business leveraging optimum resources utilization can finally have what they are looking for.
Try Xeoma for free! Enter your name and your email to send the license to in the fields below, and click the ‘Get Xeoma free demo licenses to email’ button.
We urge you to refrain from using emails that contain personal data, and from sending us personal data in any other way. If you still do, by submitting this form, you confirm your consent to processing of your personal data
|
|
Starting with October 2025 Xeoma Starter licenses may be purchased only in bulk (quantity 100 or above). If you’d like to make this purchase, please contact us. |
21 August, 2021
Read also:
DIY home security system with video surveillance program Xeoma
Complete Xeoma User Manual
Let’s get it started, or how to use Xeoma
Video surveillance for business and major systems
Video surveillance for home usage or for small systems
Xeoma Video Surveillance System video tutorials
Xeoma for Mac: installation guide
Xeoma for Linux: installation and work